WARNING: A newer version of ModSecurity is available. The article to install ModSecurity 3 on FreeBSD can be found here. Will be published on March 1st, 2021. If you find the articles in Adminbyaccident.com useful to you, please consider making a donation. Use this link to get $200 credit at DigitalOcean and support Adminbyaccident.com costs. […]

How to install ModSecurity 2 on FreeBSD

How to mitigate/solve the MDS vulnerabilities of Intel processors in FreeBSD
It had to happen again. Anyone betting on new hardware vulnerabilities on Intel processors would have won. This time these are called the MDS vulnerabilities, which stands for Microarchitectural Data Sampling. The trouble is the ones who would have really made big money would have been those stating the new CPUs were on the same […]
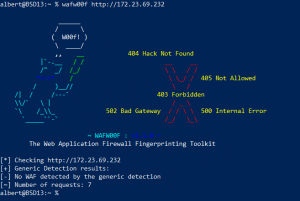
How to detect a WAF – Web Application Firewall
From a penetration testing perspective to identify if a Web Application Firewall (WAF) is in place is essential. The next question is, does an administrator need to know this? My view is, anyone who is in charge of any system that has implemented some sort of WAF needs to verify this tool is working, at […]

How to install Nessus 10 on FreeBSD 12
Nessus is a professional vulnerability scanner from the reputable cybersecurity company Tenable. I have already written about it in the past but installing it on a GNU/Linux distro. This very article will guide anyone to install Nessus 10 on FreeBSD, since Tenable is releasing binaries for FreeBSD 11 and 12 as of the time of […]

Absolute FreeBSD 3rd Edition Book Review
Absolute FreeBSD 3rd Edition from Michael W. Lucas, printed by ‘No Starch Press’, is an absolute (pun intended) must have for every BSD user and I’d go so far as to say to every UNIX and Linux user indeed. If you find the articles in Adminbyaccident.com useful to you, please consider making a donation. Use […]
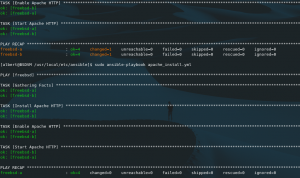
How to install Ansible on FreeBSD
Ansible is a very useful tool geared to system’s configuration and applications deployment. In this how to install Ansible on FreeBSD I will briefly explain what the tool is, what it does, what it does not and how to install it on FreeBSD. I will also demonstrate very basic use and on a later article […]
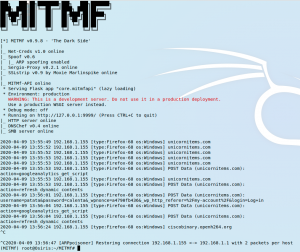
ARP spoofing attacks
ARP spoofing attacks are quite harming and they can easily constitute a man-in-the-middle (MITM) attack. They consist on the attacker sending ARP packets into the network the victim is located, typically redirecting traffic to the attacker’s machine. Once this is achieved the attacker can sniff all the traffic sent by the victim’s device and obtain […]

The LAMP stack (Debian 9)
LAMP stack stands for a software stack composed by Linux, Apache, MySQL and PHP (or Perl). It is used for many purposes and its common ground for system administrators. Since there are several of Linux distributions there are some differences in the way the LAMP stack is installed. In this guide we are using the […]

How to mitigate Spectre and Meltdown on a Lenovo T430s laptop with Ubuntu
As recently announced in a previous article I wanted to write a couple of guides on how to mitigate Spectre and Meltdown vulnerabilities in GNU/Linux and UNIX environments. It is always a good and I hope a standard practice to have your systems patched and if they aren’t for whatever the reason (that legacy thing […]
How to install Webmin on FreeBSD 12
Webmin is a fantastic tool for those willing to administer UNIX or unix-like systems through a GUI interface. While the CLI interface lets any user to interact with these kind of systems to the very core and extract all the juice, there are tasks where the graphical interface makes sense and its visual and quick […]