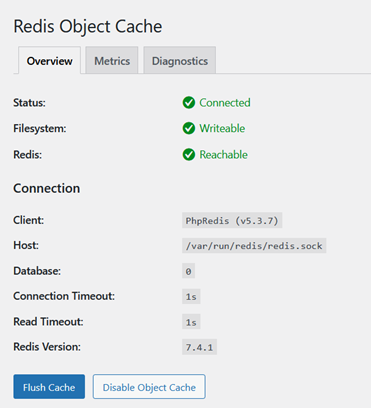
Apache HTTP as a reverse proxy consists on setting an Apache HTTP server as a frontal access for one or multiple backend servers. In the recent years many have started using NGINX as a reverse proxy since this piece of software really shines for serving static content an acting as a cache server. This doesn’t […]
How to configure Apache HTTP as a reverse proxy on FreeBSD
How to mitigate DoS attacks with mod_evasive on FreeBSD
Denial of Service attacks or the distributed version of them (DDoS) have been growing throughout the years with their ups and downs. In my view the only thing that will happen to them is even bigger growth. With the advent of IoT devices the next decade will see an increase in these kind of attacks. […]
How to set time and date in FreeBSD
In a FreeBSD system one may need to adjust date and time, specially if one has opened a VPS instance in some hosting provider. The system already provides a list of time zones. Just look around in the /usr/share/zoneinfo folder and subfolders to find the one that fits your needs. Just remember this will have […]
Networking Dictionary
This is an attempt to collect all the necessary basic vocabulary to have a very basic basic understanding of networking. Because context is also needed, some concepts or historical references will be also shown. This dictionary is an informal one, for a better, accurate, more correct and in depth understanding look somewhere else, like the […]

What is UNIX?
UNIX is an operating system. And your known equivalent is Windows or the Mac. You may even know about Linux. The purpose of an OS is to accommodate programs in order to get some work done. Editing pictures, browsing the web or serving data from a database. It is the thing that lets you operate […]
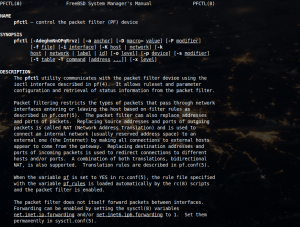
How to configure the PF firewall on FreeBSD
There are three firewall options on FreeBSD. The in-house built IPFW, the ‘old’ IPF (known as IP Filter) and PF ported from OpenBSD. PF is a very popular piece of software which was originally sparked from an issue on the IPF license that prevented making changes publicly available, which the OpenBSD did all the time. […]
How to install Nextcloud on FreeBSD 12
Nextcloud. Have you heard of it? That’s quite probable if you’re here. But, what is it, what is it? Some say it is a Google Apps replacement, some say it’s just a place to store your documents, some others just rely on it to share documents across the company and edit them just in time […]
The root account
Users. What the hell you mean by “root”? Are you a Windows user? I bet you have the user account badly configured. By default Windows is installed under the Administrator account. And nobody bothers to change this and add a second account. That second account should be an underprivileged one. If you own the computer […]
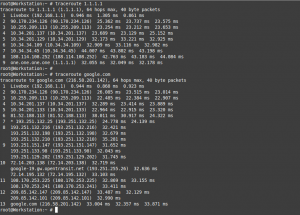
A few useful network commands
Troubleshooting network issues with simple commands is not a very difficult topic once there is a little toolbox to pull from. Needless to say networking topics can be very complicated and any specialist on the field will tell you how cumbersome it can really get. However with a few set of commands one can get […]

Monitoring Systems (One)
Monitoring systems or how to get lost in fierce madness. There are many solutions to monitor systems and most of them have some kind of web interface to operate. Choosing the right tool for any job is a tedious task and for a newbie like me it is a bit harder, specially for a sensitive […]