The default version of OpenSSH in FreeBSD 12.2 today, and it’s been this for quite some time, is not the most recent published by the OpenBSD guys, which by the way are the ones developing OpenSSH. Not only is not the latest but it has a few vulnerabilities affecting it, medium risk ones but nevertheless they exist. In this short article I pretend to show how to check if the system is affected and how to patch OpenSSH in FreeBSD.
If you find the articles in Adminbyaccident.com useful to you, please consider making a donation.
Use this link to get $200 credit at DigitalOcean and support Adminbyaccident.com costs.
Get $100 credit for free at Vultr using this link and support Adminbyaccident.com costs.
Mind Vultr supports FreeBSD on their VPS offer.
Don’t panic or think the FreeBSD folks are nuts to release their OS with a vulnerable OpenSSH in the base system that is easy to exploit.
First things first, we’ll check the operating system version.
[albert@BSDVM ~]$ freebsd-version
12.2-RELEASE-p2
[albert@BSDVM ~]$
As of today, January the 2nd of 2021, this system is the most recent release of FreeBSD. Now we’ll check the current OpenSSH version in this system. Notice this is the default in the system.
[albert@BSDVM ~]$ ssh -V
OpenSSH_7.9p1, OpenSSL 1.1.1h-freebsd 22 Sep 2020
[albert@BSDVM ~]$
Now this is clear, we can use some tooling to check if there are any vulnerabilities in the system. In this case the tool is nmap. Let’s install it.
[albert@BSDVM ~]$ sudo pkg install -y nmap
Updating FreeBSD repository catalogue...
FreeBSD repository is up to date.
All repositories are up to date.
The following 1 package(s) will be affected (of 0 checked):
New packages to be INSTALLED:
nmap: 7.91
Number of packages to be installed: 1
The process will require 26 MiB more space.
6 MiB to be downloaded.
[1/1] Fetching nmap-7.91.txz: 100% 6 MiB 2.0MB/s 00:03
Checking integrity... done (0 conflicting)
[1/1] Installing nmap-7.91...
[1/1] Extracting nmap-7.91: 100%
[albert@BSDVM ~]$
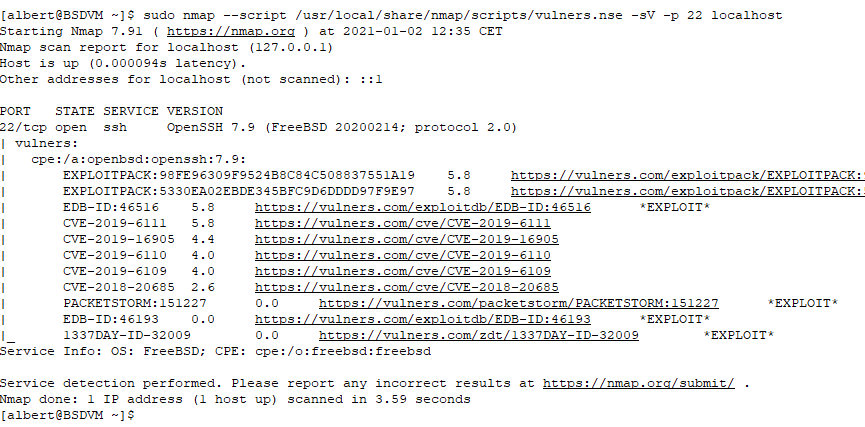
Now it is installed we’ll launch one of the internal scripts so we can look for any vulnerabilities affecting open ports. I will specifiy the ssh port here but one can avoid using it and any open ports we’ll be checked by the script. If any vulnerabilities are detected they will be displayed on the screen.
[albert@BSDVM ~]$ sudo nmap --script /usr/local/share/nmap/scripts/vulners.nse -sV -p 22 localhost
Starting Nmap 7.91 ( https://nmap.org ) at 2021-01-02 12:35 CET
Nmap scan report for localhost (127.0.0.1)
Host is up (0.000094s latency).
Other addresses for localhost (not scanned): ::1
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9 (FreeBSD 20200214; protocol 2.0)
| vulners:
| cpe:/a:openbsd:openssh:7.9:
| EXPLOITPACK:98FE96309F9524B8C84C508837551A19 5.8 https://vulners.com/exploitpack/EXPLOITPACK:98FE96309F9524B8C84C508837551A19 *EXPLOIT*
| EXPLOITPACK:5330EA02EBDE345BFC9D6DDDD97F9E97 5.8 https://vulners.com/exploitpack/EXPLOITPACK:5330EA02EBDE345BFC9D6DDDD97F9E97 *EXPLOIT*
| EDB-ID:46516 5.8 https://vulners.com/exploitdb/EDB-ID:46516 *EXPLOIT*
| CVE-2019-6111 5.8 https://vulners.com/cve/CVE-2019-6111
| CVE-2019-16905 4.4 https://vulners.com/cve/CVE-2019-16905
| CVE-2019-6110 4.0 https://vulners.com/cve/CVE-2019-6110
| CVE-2019-6109 4.0 https://vulners.com/cve/CVE-2019-6109
| CVE-2018-20685 2.6 https://vulners.com/cve/CVE-2018-20685
| PACKETSTORM:151227 0.0 https://vulners.com/packetstorm/PACKETSTORM:151227 *EXPLOIT*
| EDB-ID:46193 0.0 https://vulners.com/exploitdb/EDB-ID:46193 *EXPLOIT*
|_ 1337DAY-ID-32009 0.0 https://vulners.com/zdt/1337DAY-ID-32009 *EXPLOIT*
Service Info: OS: FreeBSD; CPE: cpe:/o:freebsd:freebsd
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 3.59 seconds
[albert@BSDVM ~]$
As it can be read there are a few vulnerabilities and exploits ready to get on a few of those. Notice all the vulnerabilities qualify as medium rated ones but when exploits exists it is recommended to patch them anyway. If anyone wants to check more information on these vulnerabilities the National Vulnerability Database (USA) collects details not just on the vulnerabilities but on the methods to calculate the risks and scores.
Fortunately for us there’s the latest OpenSSH package from the OpenBSD folks.
[albert@BSDVM ~]$ sudo pkg search openssh
OpenSSH-askpass-1.2.4.1_3 Graphical password applet for entering SSH passphrase
lxqt-openssh-askpass-0.16.0 LXQt GUI dialog for OpenSSH authentication
openssh-portable-8.4.p1_3,1 The portable version of OpenBSD's OpenSSH
openssh-portable-gssapi-8.4.p1_3,1 The portable version of OpenBSD's OpenSSH
openssh-portable-hpn-8.4.p1_3,1 The portable version of OpenBSD's OpenSSH
p5-Net-OpenSSH-0.80 Perl SSH client package implemented on top of OpenSSH
p5-Net-OpenSSH-Parallel-0.14 Run SSH jobs in parallel
[albert@BSDVM ~]$
And we can install this hilighted package to patch these vulnerabilities.
[albert@BSDVM ~]$ sudo pkg install openssh-portable
Updating FreeBSD repository catalogue...
FreeBSD repository is up to date.
All repositories are up to date.
The following 6 package(s) will be affected (of 0 checked):
New packages to be INSTALLED:
hidapi: 0.8.0.r1_3
ldns: 1.7.1_1
libcbor: 0.8.0
libcjson: 1.7.14
libfido2: 1.5.0_1
openssh-portable: 8.4.p1_3,1
Number of packages to be installed: 6
The process will require 9 MiB more space.
2 MiB to be downloaded.
Proceed with this action? [y/N]: y
[1/6] Fetching openssh-portable-8.4.p1_3,1.txz: 100% 779 KiB 797.4kB/s 00:01
[2/6] Fetching libfido2-1.5.0_1.txz: 100% 152 KiB 155.3kB/s 00:01
[3/6] Fetching libcbor-0.8.0.txz: 100% 29 KiB 30.1kB/s 00:01
[4/6] Fetching libcjson-1.7.14.txz: 100% 34 KiB 34.5kB/s 00:01
[5/6] Fetching hidapi-0.8.0.r1_3.txz: 100% 32 KiB 33.1kB/s 00:01
[6/6] Fetching ldns-1.7.1_1.txz: 100% 515 KiB 527.5kB/s 00:01
Checking integrity... done (0 conflicting)
[1/6] Installing libcjson-1.7.14...
[1/6] Extracting libcjson-1.7.14: 100%
[2/6] Installing libcbor-0.8.0...
[2/6] Extracting libcbor-0.8.0: 100%
[3/6] Installing hidapi-0.8.0.r1_3...
[3/6] Extracting hidapi-0.8.0.r1_3: 100%
[4/6] Installing libfido2-1.5.0_1...
[4/6] Extracting libfido2-1.5.0_1: 100%
[5/6] Installing ldns-1.7.1_1...
[5/6] Extracting ldns-1.7.1_1: 100%
[6/6] Installing openssh-portable-8.4.p1_3,1...
[6/6] Extracting openssh-portable-8.4.p1_3,1: 100%
=====
Message from openssh-portable-8.4.p1_3,1:
--
To enable this port, add openssh_enable="YES" in your rc.conf. To
prevent conflict with openssh in the base system add sshd_enable="NO"
in your rc.conf. Also you can configure openssh at another TCP port (via
sshd_config 'Port' and 'Listen' options or via 'openssh_flags'
variable in rc.conf) and run it in same time with base sshd.
'PermitRootLogin no' is the default for the OpenSSH port.
This now matches the PermitRootLogin configuration of OpenSSH in
the base system. Please be aware of this when upgrading your
OpenSSH port, and if truly necessary, re-enable remote root login
by readjusting this option in your sshd_config.
Users are encouraged to create single-purpose users with ssh keys, disable
Password authentication by setting 'PasswordAuthentication no' and
'ChallengeResponseAuthentication no', and to define very narrow sudo
privileges instead of using root for automated tasks.
[albert@BSDVM ~]$
Notice this package is the 8.4 version and the one in the base system is the 7.9.
Now we get to the dangerous part. Be aware applying this change there’s the possibility to lose SSH connectivity so one may find oneself logged out without possibility to get back into the system unless we have direct physical access or a browser console such as those found on services like Digital Ocean.
The order of these next steps is important in this how to patch OpenSSH in FreeBSD process. If we disable the ‘sshd’ service before stopping it we won’t be able to stop it, unless we use the ‘kill’ command. Then we’ll have to enable the new openssh package and start the service. If we log out in the middle of this process we won’t be able to log in back again. If we read the install instructions we can also use a different port for the newly installed OpenSSH package, so we never loose the chance to log back in following those other instructions.
We now stop the sshd service.
[albert@BSDVM ~]$ sudo service sshd stop
Stopping sshd.
[albert@BSDVM ~]$
Once it’s stopped we will add the new openssh package to be started as a service at boot time.
[albert@BSDVM ~]$ sudo sysrc openssh_enable="YES"
openssh_enable: -> YES
[albert@BSDVM ~]$
Now it’s time to edit the /etc/rc.conf file and disable the base system’s ssh service.
[albert@BSDVM ~]$ sudo vi /etc/rc.conf
hostname="BSDVM"
keymap="es.acc.kbd"
ifconfig_em0="DHCP"
sshd_enable="NO"
ntpdate_enable="YES"
# Set dumpdev to "AUTO" to enable crash dumps, "NO" to disable
dumpdev="NO"
zfs_enable="YES"
ntpd_enable="YES"
ntpd_sync_on_start="YES"
openssh_enable="YES"
[albert@BSDVM ~]$
The final step is to start the new openssh service.
[albert@BSDVM ~]$ sudo service openssh start
Generating public/private dsa key pair.
Your identification has been saved in /usr/local/etc/ssh/ssh_host_dsa_key
Your public key has been saved in /usr/local/etc/ssh/ssh_host_dsa_key.pub
The key fingerprint is:
SHA256:CVgVvvjv9EXpQ93vcLUNLNL+DuOnT8fVvun7EOWQgTU root@BSDVM
The key's randomart image is:
+---[DSA 1024]----+
| ..o. oE |
| o . . + |
| . . . o .|
| o o . . *o|
| . S . o B B|
| . o = =*|
| . . + B.B|
| o o *.Bo|
| .o +====|
+----[SHA256]-----+
Generating public/private rsa key pair.
Your identification has been saved in /usr/local/etc/ssh/ssh_host_rsa_key
Your public key has been saved in /usr/local/etc/ssh/ssh_host_rsa_key.pub
The key fingerprint is:
SHA256:oUxJHtq9gHZBRiDeVY4CASc7UkdLg4a0qu9Li346BT0 root@BSDVM
The key's randomart image is:
+---[RSA 3072]----+
|++*+*+O.. |
|.*+* @ B |
|+oo B O + |
|oo E = o o |
|. . . o S |
|. . |
|. o |
| = o |
|o+O. |
+----[SHA256]-----+
Generating public/private ecdsa key pair.
Your identification has been saved in /usr/local/etc/ssh/ssh_host_ecdsa_key
Your public key has been saved in /usr/local/etc/ssh/ssh_host_ecdsa_key.pub
The key fingerprint is:
SHA256:k1Vy4kjqlFCforpnMz/JaKF7hVtwn3bSv7yHolbbTvY root@BSDVM
The key's randomart image is:
+---[ECDSA 256]---+
| ... . o o |
| . = + = |
| = + o |
| .+.. o |
| .+..So |
| .o o =.+ |
| .. B o + +o. |
| ..X + . o++.. |
| o* +.o.. o=+E |
+----[SHA256]-----+
Generating public/private ed25519 key pair.
Your identification has been saved in /usr/local/etc/ssh/ssh_host_ed25519_key
Your public key has been saved in /usr/local/etc/ssh/ssh_host_ed25519_key.pub
The key fingerprint is:
SHA256:JoVQGjwhEBb5bCRhsaxmyYk/AVfs+sU2aY6KONoLuno root@BSDVM
The key's randomart image is:
+--[ED25519 256]--+
|oO*o=o. |
|+o.+++ . |
|.o*.... . |
|+oo+. . |
|o*o. ...S |
|o... Bo |
|. o. * . |
|++E.o . |
|X++o |
+----[SHA256]-----+
Performing sanity check on openssh configuration.
Starting openssh.
[albert@BSDVM ~]$
Now that we have changed our SSH service version from 7.9 to the more up to date 8.4 we can log into the system with a different user so we are sure we haven’t lost SSH connectivity.
Once we are sure we can log into the system with these changes we can check if there are any vulnerabilities to port 22 as we’ve tested before.
[albert@BSDVM ~]$ sudo nmap --script /usr/local/share/nmap/scripts/vulners.nse -sV -p 22 localhost
Starting Nmap 7.91 ( https://nmap.org ) at 2021-01-02 14:06 CET
Nmap scan report for localhost (127.0.0.1)
Host is up (0.00013s latency).
Other addresses for localhost (not scanned): ::1
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.4 (protocol 2.0)
Service Info: OS: FreeBSD; CPE: cpe:/o:freebsd:freebsd
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 4.46 seconds
[albert@BSDVM ~]$
As we can see now there are no vulnerabilities affecting the ssh service, so we have patched this system with the latest OpenSSH software.
This nmap script can be used without specifying the port number by removing the ‘-p’ flag and port number, so all the accessible ports will be checked. In combining this with the Lynis software and other programs such as Nessus, we have nice auditing pieces. Of course we can complete this with more tooling, but these are good ones to start with.
Mind we now have to configure the ssh service somewhere else and not in the default ‘/etc/ssh/sshd_config’ file since we are now using the package option and not the base system one. Where to find this? Here, in this path below:
[albert@BSDVM ~]$ ll /usr/local/etc/ssh
total 156
drwxr-xr-x 2 root wheel 16B 2 gen. 12:22 .
drwxr-xr-x 11 root wheel 21B 2 gen. 12:19 ..
-rw-r--r-- 1 root wheel 564K 14 des. 01:25 moduli
-rw-r--r-- 1 root wheel 564K 14 des. 01:25 moduli.sample
-rw-r--r-- 1 root wheel 1,5K 14 des. 01:25 ssh_config
-rw-r--r-- 1 root wheel 1,5K 14 des. 01:25 ssh_config.sample
-rw------- 1 root wheel 1,3K 2 gen. 12:22 ssh_host_dsa_key
-rw-r--r-- 1 root wheel 600B 2 gen. 12:22 ssh_host_dsa_key.pub
-rw------- 1 root wheel 505B 2 gen. 12:22 ssh_host_ecdsa_key
-rw-r--r-- 1 root wheel 172B 2 gen. 12:22 ssh_host_ecdsa_key.pub
-rw------- 1 root wheel 399B 2 gen. 12:22 ssh_host_ed25519_key
-rw-r--r-- 1 root wheel 92B 2 gen. 12:22 ssh_host_ed25519_key.pub
-rw------- 1 root wheel 2,5K 2 gen. 12:22 ssh_host_rsa_key
-rw-r--r-- 1 root wheel 564B 2 gen. 12:22 ssh_host_rsa_key.pub
-rw-r--r-- 1 root wheel 3,1K 14 des. 01:25 sshd_config
-rw-r--r-- 1 root wheel 3,1K 14 des. 01:25 sshd_config.sample
[albert@BSDVM ~]$
One will have to make the configuration arrengements one had in the previous base system in here. So, this could be done just after the install of the openssh-portable package. Then, once configured, one can apply the software change process without losing the desired configuration not for a second.
This is all for this how to patch OpenSSH in FreeBSD and I hope this can help anyone.
If you find the articles in Adminbyaccident.com useful to you, please consider making a donation.
Use this link to get $200 credit at DigitalOcean and support Adminbyaccident.com costs.
Get $100 credit for free at Vultr using this link and support Adminbyaccident.com costs.
Mind Vultr supports FreeBSD on their VPS offer.